Email is fundamentally insecure. There are such a plethora of issues with it, it is crazy to think about the kind of information sent with it. It is probably even crazier when you realize we’ve had a solution for sending secure email since 1991.
Fundamental issues with email
There’s lots of fundamental issues with email. Here are some of them:
1. Email travels and is stored in plain text
This means that anyone managing a server or network device along the way can read (and modify) the email as they like. You may compare it to sending a postcard by regular mail. Any information in it should be regarded as publicly available. Ever heard of “leaked emails”? Yeah. It doesn’t take much of a hacker to do that.
2. There are no integrity checks
When you send an email, you don’t know whether it will end up at the recipient without modification. The recipient can’t trust the content, as they can’t be assured it haven’t been modified along the way. This happens much more than you think. Usually “just” some tracking code or ads are inserted.
3. There is no sender verification
Ever heard of phishing? Do you know how to impose as someone? Go into your email client and change the email address. Now you can send emails on behalf of that person. Usually, there is no way to detect if an email was really sent by someone or not.
Pretty Good Privacy (PGP)
Now, go more than two and a half decades back, to 1991. Phil Zimmermann is very much aware of these issues with email and invents a solution he calls Pretty Good Privacy, or PGP for short. PGP provides cryptographic privacy and authentication for just about any data.
PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications.
It works like this:
Cryptographic key pair
You create a cryptographic key pair. This pair consists of a private and a public key. The private key must be kept really, really secret and secure. The public key should be made as publicly available as possible: Uploaded to special key servers and posted on your blog and social media profiles.
Encrypted content
When someone wants to send you an email, they encrypt it with your public key. Only the secret key can be used to decrypt the contents. This means that only you can read the content.
Digital signature
Also, whether you choose to encrypt the content or not, you can digitally sign the email message you’re sending. Then you use your private key to generate and attach a signature based on the content of the email message. The recipient can then use your public key to verify that the signature was really made with your private key – thus really signed by you. This verifies both the sender and the content. If the signature doesn’t match with both the sender and the content, something phishy is going on.
Pretty good, but not full privacy
Encryption and signing solve all three issues I mentioned at the beginning. However, PGP doesn’t provide full privacy: Headers are still public. This includes info on who sent it, when they sent it, and possibly where did they send it from.
OpenPGP and GnuPG are free
Since 1997 there has been an open standard for PGP encryption called OpenPGP. This is the standard everybody is using today, and you don’t really have to worry about any incompatibilities at all.
GNU Privacy Guard (GnuPG or GPG) is a free software implementation of OpenPGP and is interoperable and compatible with other OpenPGP-compliant software.
In general, the terms GnuPG, GPG, GNU Privacy Guard, OpenPGP and PGP are used interchangeably. Technically, OpenPGP (Pretty Good Privacy) is the encryption standard, and GNU Privacy Guard (often shortened to GPG or GnuPG) is the program that implements the standard.
– Free Software Foundation
Why doesn’t everybody use secure email?
I don’t know. Maybe too difficult to get started with? Concept to advanced to understand? Not reached critical mass? Beats me. It’s not really difficult to get started, and when you are up and running, it is really easy to use.
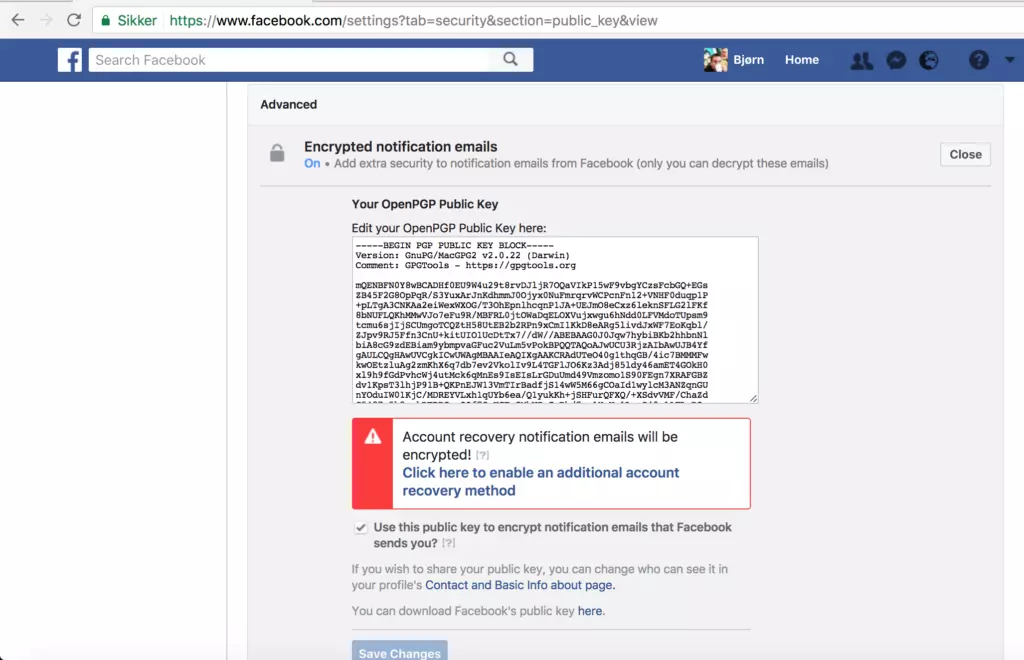
With all kinds of email scandals, spear phishing attacks and corporate and governmental surveillance schemes, there seems to me that secure email has gotten more popular the last few years. More and more people and services are using it. Even Facebook will send you all emails encrypted and signed if you enter your public key in your profile settings. No more Facebook account phishing attacks for you!
How to get started with secure email
The Free Software Foundation has published an excellent step-by-step tutorial that guides you through the steps, explaining everything nicely along the way. Just select if you use GNU/Linux, MacOS or Window at the top. You’ll find the guide “Email Self Defence” here.
Send me a secure email message
If you want to send me an email, my fingerprint is:
5029 E0D0 F458 72E4 09D3 308D 1D51 378E E348 35B6 My full OpenPGP (GnuPG) public key is also available here.
Good luck, have fun and stay safe!
